While there is no single, universally agreed-upon number, it's most effective to think of hardening not as a list of techniques but as a discipline organized into several core domains. These domains encompass securing everything from the network connection and the operating system to the specific applications and databases running on the system.
The most critical insight is that system hardening is a multi-layered strategy, not a single action. True security comes from applying a consistent set of principles across every layer of your technology stack, from the network to the application itself.

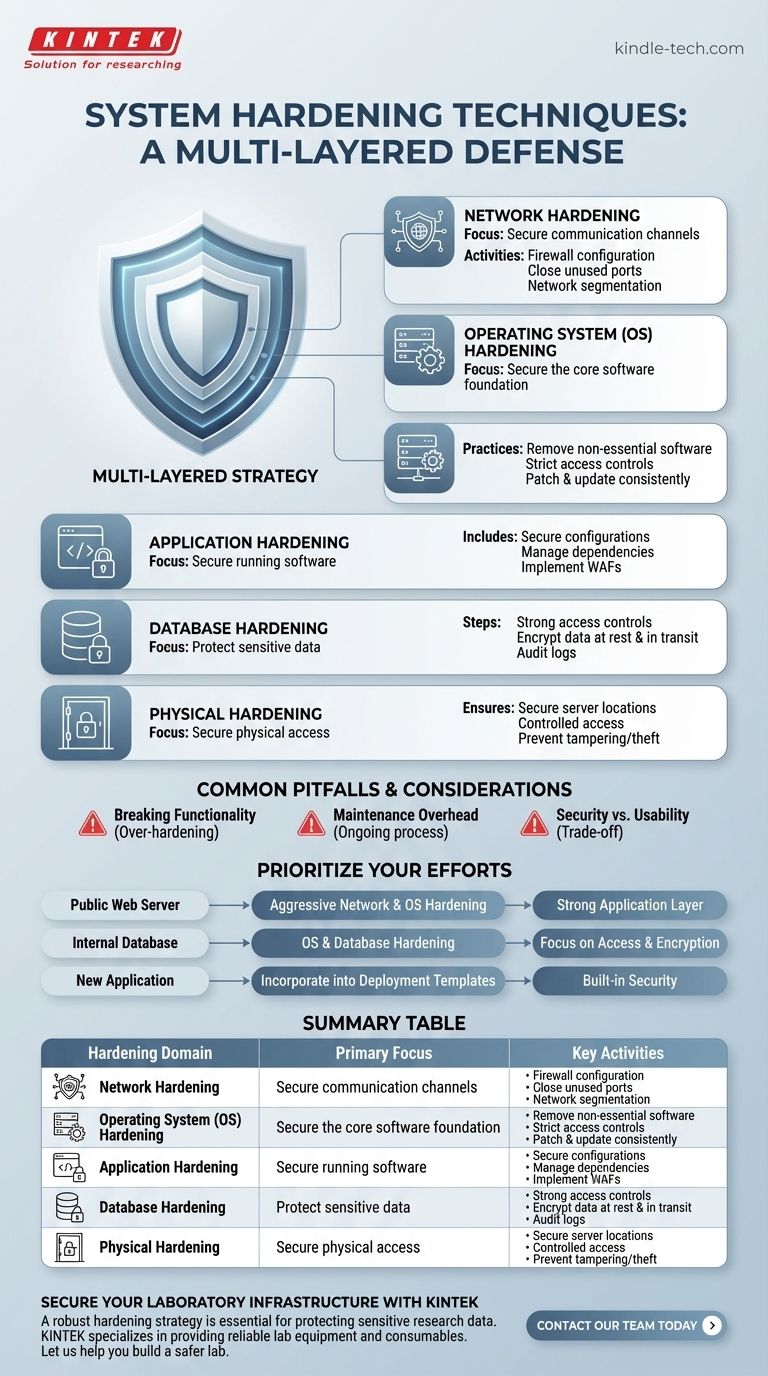
The Core Pillars of System Hardening
System hardening is the process of reducing a system's "attack surface" by eliminating potential security vulnerabilities. This is achieved by applying a defense-in-depth approach across several distinct but interconnected areas.
1. Network Hardening
This domain focuses on securing the communication channels to and from your servers. It is often the first line of defense against external threats.
Key activities include implementing and configuring firewalls to control traffic, closing all unnecessary network ports, and using network segmentation to isolate critical systems from less secure ones.
2. Operating System (OS) Hardening
This is the foundation of server security, focusing on the core software that manages the hardware and resources. A compromised OS provides an attacker with broad control.
Common practices involve removing all non-essential software and services, implementing strict user access controls (Principle of Least Privilege), and ensuring the OS is consistently patched and updated.
3. Application Hardening
Applications are often the most direct point of interaction for users and, therefore, a prime target for attackers. This layer involves securing the software running on top of the OS.
This includes securing application configurations, managing third-party dependencies for known vulnerabilities, and implementing web application firewalls (WAFs) for web-based services.
4. Database Hardening
Databases frequently store an organization's most sensitive information, from customer data to financial records. Securing them is paramount.
Essential steps include enforcing strong access controls on database users, encrypting sensitive data both at rest and in transit, and regularly auditing database logs for suspicious activity.
5. Physical Hardening
While often overlooked in the age of cloud computing, physical security remains a critical component of a comprehensive hardening strategy.
This ensures that servers and networking equipment are located in physically secure areas, such as locked server rooms with controlled access, to prevent unauthorized physical tampering or theft.
Common Pitfalls and Considerations
Implementing hardening techniques is not without its challenges. A poorly executed strategy can create more problems than it solves, highlighting the need for a balanced approach.
The Risk of Breaking Functionality
The most common pitfall is over-hardening a system. Aggressively disabling services, closing ports, or changing permissions without proper testing can easily break application dependencies and disrupt business operations.
The Maintenance Overhead
Hardening is not a one-time event. It creates an ongoing maintenance burden to manage patches, review configurations, and audit access controls, which requires dedicated time and resources.
Security vs. Usability
There is often a direct trade-off between security and usability. Highly secure systems may require complex login procedures or restricted access that can frustrate users and impede productivity if not implemented thoughtfully.
How to Prioritize Your Hardening Efforts
Your hardening strategy should be guided by the specific role of the system and the sensitivity of the data it handles.
- If your primary focus is a public-facing web server: Begin with aggressive network and OS hardening to protect against automated, external attacks, and add a strong layer of application hardening.
- If your primary focus is an internal database server: Prioritize OS and database hardening, with an extreme focus on user access controls and data encryption.
- If you are deploying a new application from scratch: Incorporate hardening into your deployment templates and automated processes to ensure security is built-in and consistent from day one.
Ultimately, effective hardening is a continuous process of risk reduction, not a quest for an unbreakable system.
Summary Table:
| Hardening Domain | Primary Focus | Key Activities |
|---|---|---|
| Network Hardening | Securing communication channels | Firewall configuration, closing unused ports, network segmentation |
| OS Hardening | Securing the core operating system | Removing non-essential services, strict access controls, patching |
| Application Hardening | Securing running software | Secure configurations, vulnerability management, WAFs |
| Database Hardening | Protecting sensitive data | Strong access controls, data encryption, activity auditing |
| Physical Hardening | Preventing physical tampering | Secure server room access, controlled environments |
Secure Your Laboratory Infrastructure with KINTEK
A robust hardening strategy is essential for protecting sensitive research data and ensuring the integrity of your lab operations. The principles of network, OS, application, and database hardening directly apply to securing the sophisticated equipment and software that power modern laboratories.
KINTEK specializes in providing reliable lab equipment and consumables, and we understand that security is a foundational component of your work. Whether you're automating processes or managing critical data, a secure environment is non-negotiable.
Let us help you build a safer lab. Our expertise can support your efforts to maintain a hardened, compliant, and efficient research environment.
Contact our team today to discuss your laboratory's specific security and equipment needs.
Visual Guide
Related Products
- Warm Isostatic Press for Solid State Battery Research
- Vacuum Hot Press Furnace Heated Vacuum Press Machine Tube Furnace
- Carbide Lab Press Mold for Laboratory Applications
- Vacuum Hot Press Furnace Machine Heated Vacuum Press
- HFCVD Machine System Equipment for Drawing Die Nano-Diamond Coating
People Also Ask
- What are the four stages of sintering? A Guide to Precise Material Densification
- What is an example of a continuous furnace? Discover the Conveyor Belt Furnace for High-Volume Production
- How does an industrial furnace work? Key Components and Applications Explained
- Why is an ultrasonic cleaner used with ethanol to treat alloy specimens? Ensure Superior Diffusion Bonding Results
- What is magnetron sputtering coating? A High-Performance Thin Film Deposition Process
- What is the best way to join stainless steel? A Guide to Welding, Brazing, and Fastening
- How thick is sputter coating for SEM? Achieve Perfect SEM Imaging with Optimal Coating Thickness
- What is the process of THC distillate? A Step-by-Step Guide to Pure Potency